CompTIA PenTest+ Certification Review
In the cybersecurity industry, certifications are a crucial part of a technical employee’s professional development. For a penetration tester, there are many certifications that can attest to one’s skillset. One of the newer certifications is CompTIA’s PenTest+, which is the organization’s take on the ever-growing penetration tester or ethical hacker market and is designed to assess penetration testing, vulnerability management, and management skills. In CompTIA’s cybersecurity pathway of certifications, PenTest+ is next in the series to Security+ and the offensive counterpart to the defensive Cybersecurity Analyst (CySA+).
In this review, we take a detailed look into the PenTest+ and walk through the preparation process, the quality of the exam content, and the similarities with related certifications. Does CompTIA have a competitive offering or is the multiple-choice exam format insufficient to verify expertise in the topic?
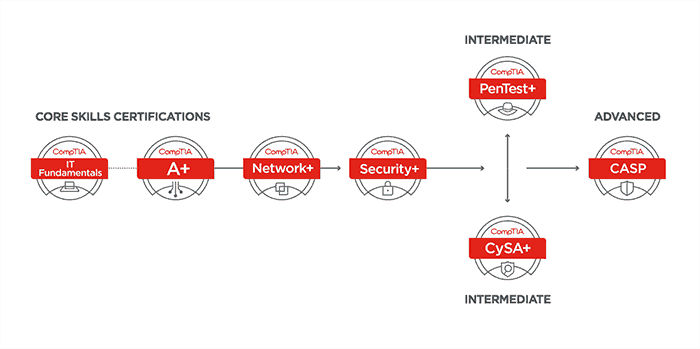
CompTIA Cybersecurity Pathway
Exam Overview
Eligibility for the PenTest+ certification is determined by a proctored exam with a mixture of multiple-choice and performance-based questions. These special performance-based questions are a combination of disguised multiple-choice questions and somewhat realistic simulations. The finer technical details concerning the exam are covered well in the Exam Objectives published by CompTIA, as well as the subject areas tested. These subject areas are composed of five domains that include both technical topics such as vulnerabilities, exploits, and tools, and non-technical material such as planning and reporting.
Exam Content and Preparation Process
Preparing for the exam is both simple and difficult. Topics of questions stay inside of the published objectives, so test takers would do well to review it and use it as a launching point for further study. However, the real challenge in preparation comes from the nature of the test. It is absolutely necessary to have hands-on experience to make sense of many of the questions; textbook study is insufficient. While some of the questions have plain textbook answers, many of them require a familiarity with the topic that comes from realistic, practical experience.
However, typical pentesting skills will only take someone so far. Aside from knowledge of common tools such as nmap, netcat and Metasploit, test takers should practice in lesser-traveled territories of pentesting such as mobile application and wireless. Just because a typical pentest may only include web applications and operating system vulnerabilities does not mean CompTIA has neglected less frequently encountered security issues.
Another unexpected emphasis of the exam is scripting. While scripting skills are not necessary for a good pentester, they are for an efficient one. CompTIA isn’t looking for complete expertise, but fluency in Bash, Python, Ruby, Perl and PowerShell as well as the ability to differentiate between all of them is necessary for a portion of the exam.
Quality of Exam Questions
Overall, the exam does well to cover not only the advertised domains but also provides rather comprehensive coverage of the subject matter of penetration testing. In other words, a certification holder will have at least an entry-level competence in multiple kinds of pentests. As mentioned before, the experience requirement inherent to many of the questions will weed out candidates who have only crammed textbooks and study guides.
The performance-based questions introduce some novel testing formats, such as auditing a website’s certificate and source code, piecing together the commands and options that created displayed output, and dragging and dropping blocks of scripting code together to perform a task. Others are simply multiple-choice questions in a different skin and probably should not be passed off as “performance-based” challenges.
The “difficulty by vague wording” questions seen in other CompTIA exams like Security+ are fortunately few and far between here, with right answers being clearer to those who understand the topic well. Unfortunately, there are a handful of “spot the minor syntax error” questions that may be difficult for those who have not memorized whichever tool or procedure is being tested on. These questions are not as helpful as the more differentiated questions, since they test on flash card memorization rather than working knowledge.
While there are some annoyances in the formatting and structure of questions, for the most part the exam is well constructed, even improving on some of CompTIA’s other offerings.
Industry Impact and Exam Comparison
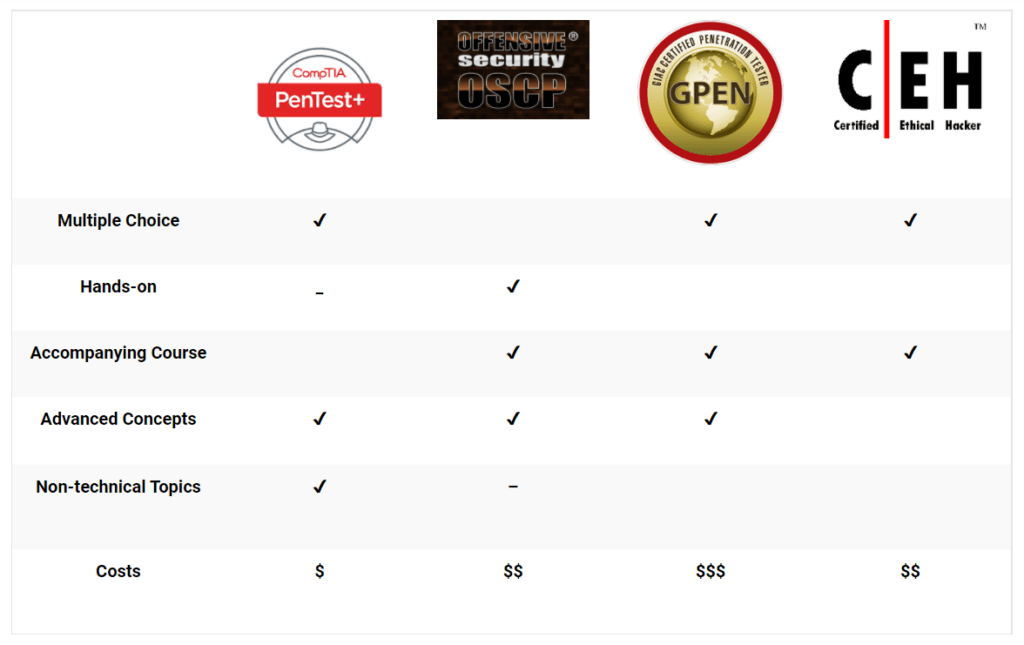
It is too early to definitively say what kind of impact the PenTest+ will have on the information security industry, but there is room for speculation. It would appear that it is aimed to compete with other beginner to intermediate certifications in the penetration tester space, such as the Offensive Security Certified Professional (OSCP), the GIAC Penetration Tester (GPEN), and EC Council’s Certified Ethical Hacker (CEH).
OSCP
Compared to the OSCP, the PenTest+ has some conceptual overlap, but is ultimately a precursor rather than an equivalent. The OSCP’s exam is entirely hands-on, making it a more definitive proof of skill, and takes on more advanced concepts, such as performing buffer overflows. One advantage the PenTest+ has is its coverage of nontechnical business and project concepts, which the OSCP only lightly touches on. The cost of the OSCP is between double and triple the CompTIA exam, but it includes a full course and lab access to practice.
GPEN
The GPEN is probably the most comparable to the PenTest+ in both format (multiple-choice) and content, although it has more of a technical focus. While CompTIA provides study material for all their certifications, GIAC certifications have accompanying SANS training courses that are highly reputable and fully inclusive of the exam content. This comes at a cost, however, as the exams and courses are notoriously expensive.
CEH
The PenTest+ appears to be created to take on the same industry requirements that the CEH meets, but that is where the similarities end. The CEH is marketed as a penetration testing certification but ends up being a vocabulary test on hacking tools. Comparing it with CompTIA’s latest offering is inappropriate, as the CEH’s difficulty is more on par with the Security+. EC Council charges more than double CompTIA does for an exam but includes a training course.
Can PenTest+ Become an Industry Favorite?
Overall, the PenTest+ stands its ground among its peers. It won’t be replacing the OSCP, but the two can coexist with the OSCP as a requirement for experienced pentester job positions and the CompTIA certification for entry to intermediate level. If CompTIA can leverage its reputation with its other certifications, the organization has potential to sell the PenTest+ as an affordable replacement for the GPEN. Likewise, meeting the same requirements as the CEH may allow the PenTest+ to dethrone the CEH as HR’s preferred resume bullet point.
Again, the PenTest+ has done a respectable job of testing for real-world experience, so much so that it has a good chance at becoming one of the industries favored certifications.
Note: This review was written for the beta exam. While it is likely for there to be differences between it and the production version, it is unlikely for the differences to be major, meaning this review should remain pertinent.
Links:
https://certification.comptia.org/certifications/pentest
https://certification.comptia.org/certifications/security
https://certification.comptia.org/certifications/cybersecurity-analyst
https://www.offensive-security.com/information-security-certifications/oscp-offensive-security-certified-professional/
https://www.giac.org/certification/penetration-tester-gpen
https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/




