May 21, 2024
Stopping Ransomware By Managing Third-Party Risks
Hardly a day goes by when you don’t hear about a ransomware attack that has had a devastating impact on a leading company. With these attacks on the rise, it’s not enough to simply shore up your organization’s defenses. You need to ensure that the security of your third-party vendors is equally strong, including ransomware recovery. Your defenses are only as strong as your weakest link.
Implementing an effective Third-Party Risk Management (TPRM) program, a core aspect of vendor risk management, is crucial for preventing malware and other attacks from occurring through your vendors and partners.
In this blog post, we’ll:
- Describe the fundamentals of a strong TPRM program.
- Outline potential approaches for implementing a TPRM program in your environment.
- Summarize common challenges you’re likely to encounter.
- Explain Tevora’s approach to helping clients implement a TPRM program.
What Are the Fundamentals of a Strong TPRM Program?
Developing an effective TPRM program begins with establishing strong fundamentals. In this section, we’ll outline what we believe are the fundamental ingredients of any successful TPRM program based on our extensive experience helping our clients implement, enhance, and operate these programs.
Identify Key Stakeholders
Identify key stakeholders early on in the process of developing a TPRM program. These are the individuals and groups that will be driving and supporting your program. Here are examples of key stakeholders we would expect to have on a typical project:
- Internal Business Partners—People on your team that will be engaging with third-party vendors to onboard and manage their services. These people are often referred to as “contract owner” or “business owner.” They serve as a liaison between your organization and the third-party vendor’s Point of Contact (POC).
- Procurement—The department or person responsible for procuring vendor services for your organization.
- Legal—Among many other things, Legal plays a key role in developing and approving contracts with third-party vendors.
- Privacy—The group or person responsible for ensuring your organization is compliant with relevant privacy frameworks such as GDPR and CCPA.
- Risk Assessment—People on your security team that are responsible for performing risk assessments.
- Vendor POC—Your primary contact for a vendor.
It’s essential to ensure that all of these key stakeholders are aligned with each other and work collaboratively throughout the entire TPRM process. Make sure that you know when key stakeholders change and work with the new stakeholders closely to bring them up to speed on the process and ensure they are aligned with the process goals and objectives. Your process may need to be updated to accommodate the unique characteristics of a new key stakeholder.
Know Your Third-Party Vendors
Develop a current inventory of your third-party vendors. It can often be a challenge to identify all of the vendors that are being used across your organization. Here are four areas that we’ve found to be valuable sources of information about an organization’s third-party vendors:
- Accounts Payable. By “following the money” you are paying to third parties, you can usually identify many of your third-party vendors.
- Contracts. Reviewing your organization’s contracts is another great way to uncover third-party vendors.
- Technology Insights. Reviewing technical documentation such as data flow maps and architecture documentation is another good way to identify third-party vendors that may not have been discovered with the approaches above. For example, this approach may identify third-party “freemium” services that your organization uses but does not pay for.
- Business Survey. Surveying your business owners or product managers is a good way to identify third-party services they are aware of that may not have been surfaced by the methods above.
Categorize Your Third-Party Vendors by Risk Tier
After you’ve developed a comprehensive inventory of your third-party vendors, we recommend categorizing them into tiers based on the level of risk they present to your organization. This allows you to focus your resources on the highest-risk vendors. Here’s an example of what your tier structure might look like, along with five questions we suggest asking each vendor to help categorize them:
Third-Party Tiering
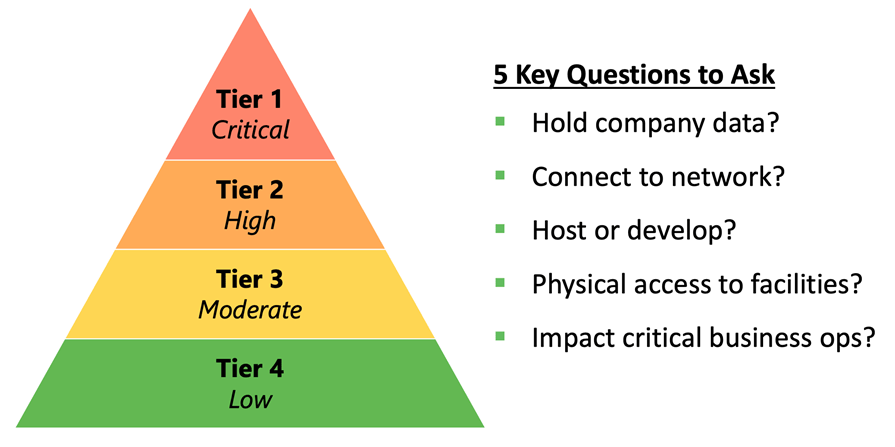
Don’t feel bound to using a four-tiered structure, as shown above. Use a number of tiers that will be helpful for your organization without creating too much complexity or administrative overhead.
Align Foundational Elements
Once you’ve taken stock of your key stakeholders, third-party vendors, and vendor risk tiers, you can start to lay out the foundation of your TPRMprogram. The three pillars of your foundation will be:
- Information Security Policy
- Contracts
- Questionnaires
This is the time to put the elements of your foundation in writing and to be preemptive and proactive. Do your best to anticipate all the situations that may arise to reduce the need for further clarification or back-and-forth down the road.
Ensure that your information security policy is integrated into your contracts and reflected in your risk assessments and questionnaires. For example, your information security policy might specify how soon a third-party vendor should notify your organization in the event of an incident. The timeframe might be based on the risk level of the vendor. This requirement should be reflected in each vendor’s contract. It should also be included in their questionnaire(s), which can be a way to verify that the vendor agrees to meet the notification timeframe requirement.
Design and Document Third-Party Vendor Processes
We recommend working with your key stakeholders to design and document the processes you will use to interact with each other. This allows you to clearly define your workflow, responsibilities, decision points, and timing while providing a clear visual image of how your process will work. It’s also an excellent opportunity to strengthen and streamline your processes.
Here’s an example of what documentation of a third-party process might look like:
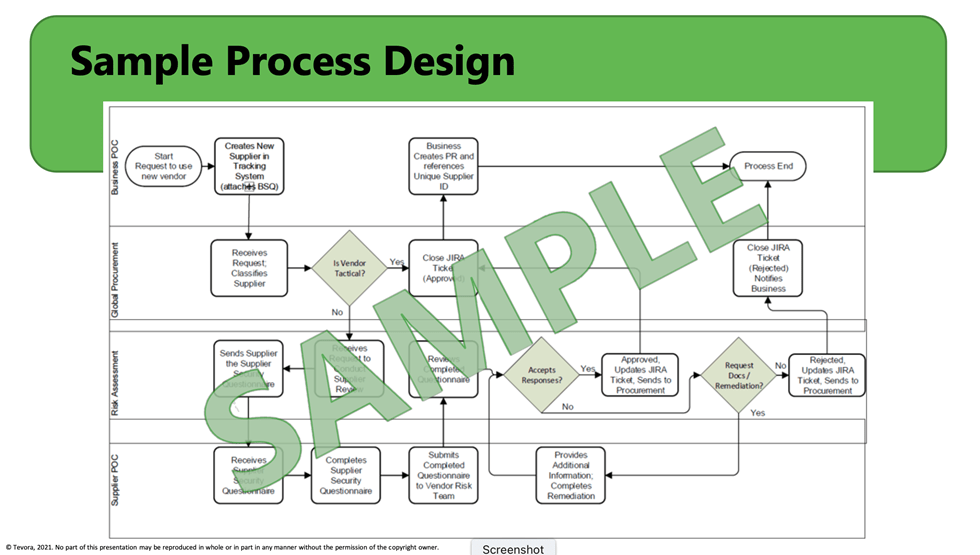
Develop Questionnaires
In addition to documenting processes, we recommend developing vendor questionnaires for processes such as onboarding, risk assessment, and procurement. This is an opportunity to flow down requirements driven by your organization’s priorities and needs, as well as security frameworks such as GDPR, DFARS, PCI, and BAA.
Ensure that your questionnaires align with and verify the requirements of your information security policies and client agreements.
Consider varying the length and complexity of your questionnaires based on the risk tier of the vendor. For example, a low-risk vendor such as your such as your coffee provider would not require a review. In contrast, a strategic vendor with which you share sensitive data may require a longer and more complex questionnaire.
Other potential considerations for questionnaires include:
- Access Control
- Data Types
- Incident Response
- Vulnerability Management
- Endpoint Controls
- Data Encryption (at rest vs. in motion)
- Third-/Fourth-Party Vendor Management
- Business Impact Analysis/Continuity
What Are the Solution Categories for Implementing a TPRM Program?
After you’ve developed your TPRM fundamentals, there are three potential approaches for implementing your program:
- In-House Management—With this approach, your organization manages all aspects of your TPRM program. This gives you full control over your vendor relationships. However, it requires a significant commitment of resources and in-house staff time.
- Shared Management Service—This approach involves outsourcing some elements of the program or processes to another organization.
- Service-Provider Management—Using this approach, you would outsource the entire TPRM process (build, develop, and maintain) to another organization.
Considerations for TPRM Tools
The solution category you use for implementing your TPRM program may impact your criteria for selecting tools to support your program. Here are some important things to consider in choosing TPRM tools:
- Integration with existing technology—Will the tool integrate well with the existing technology used by your organization or your vendors (e.g., Azure or AWS)?
- Native APIs—Do the tool’s native APIs work well with your environment or your vendors’ environment?
- Technology adoption with key stakeholders—Will your key stakeholders be able to use the tool easily, or will you need to go through months of stakeholder training?
- Realistic expectations for license usage—A common mistake is to assume that all of your vendors will require a license for the tool, when in fact, only a subset will need a one. Make sure to accurately and realistically assess how many vendor licenses will be required.
An important overarching consideration is to be sure that the tools you select will support your business processes rather than define them. In other words, don’t let the tail wag the dog.
Third-Party Risk Tool Categories
There are three main categories of third-party risk tools:
- Rating—For example, including but not limited to: RiskRecon, SecurityScorecard or BitSight. These tools give vendors a risk rating such as A, B, or C; or Strong, Moderate, or Weak.
- Exchanges—For example, including but not limited to: ProcessUnity, Pravelent, etc. These tools help you exchange documents or questionnaires between your organization and your vendors.
- Process Management—For example, including but not limited to: Prevalent, RiskRecon, ProcessUnity. These tools help you manage the third-party risk management process.
Some tools handle one or two of these categories, but none that we are aware of perform all three functions well. So, you may need to select multiple tools or combine these tools with manual processes.
What Challenges Will We Encounter When Implementing a TPRM Program?
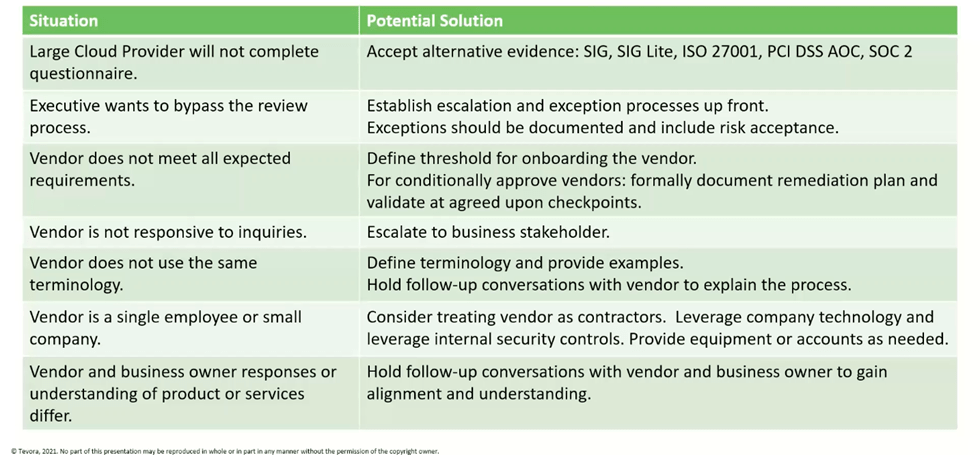
Even after you’ve developed the best-possible foundation and designed an optimal solution for your organization, you should expect to encounter challenges as you implement and manage a TPRM program. The following table summarizes common challenges we’ve encountered when helping our clients implement TPRM programs. It also presents potential solutions for each challenge.
Common Challenges and Potential Solutions
Tevora’s Approach
Based on our extensive experience helping clients implement TPRM programs, we’ve developed a streamlined, cost-effective approach, which is summarized below:

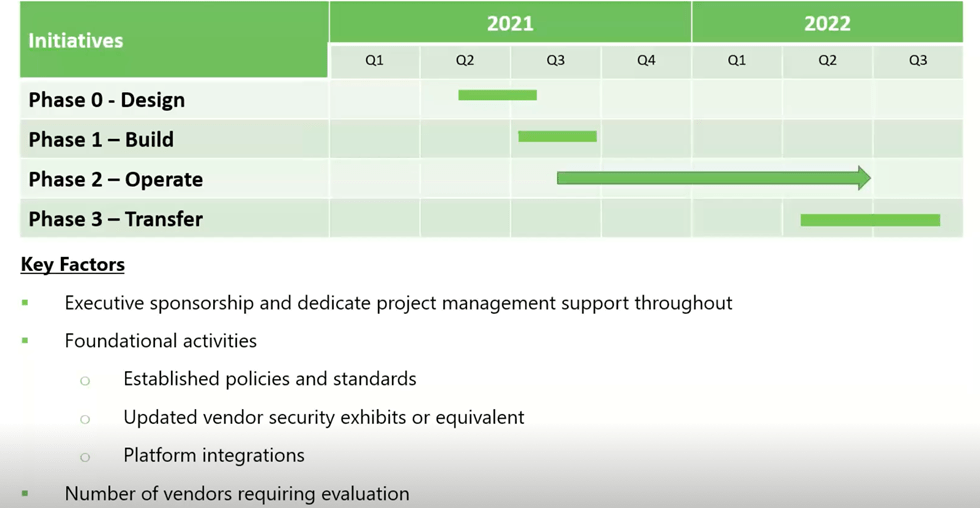
Sample Engagement Timeline
While the timeline for implementing a TPRM program for our clients will vary based on their unique business and technical environment, here’s a sample engagement timeline for a typical client:
Additional Resources
For a deeper dive on the topics covered in this blog post, check out these Tevora resources:
- Third-Party Risk Management Best Practices Webinar
- Case Study: Helping a Leading Business Services Firm Up Their Third-Party Risk Management Game
- Vendor Risk Management Datasheet
Tevora Can Help
If you have questions about Third-Party Vendor Risk Management programs or would like help implementing or improving one in your environment, just give us a call at (833) 292-1609 or email us at sales@tevora.com.