New Version 3.3 SRA Tool
If your organization handles sensitive health information, it’s likely that achieving or maintaining HIPAA compliance is high on your list of priorities. One of the most critical HIPAA requirements is to perform a risk assessment, which is key to understanding risks to the confidentiality, integrity, and availability of Protected Health Information (PHI).
Many organizations have questions about risk assessments, including:
- How do we perform one?
- What’s included?
- How will it benefit us?
The good news is that the U.S. Department of Health and Human Services (HHS), Office of Civil Rights (OCR), and the Office of the National Coordinator for Health Information Technology (ONC) has created the SRA (Security Risk Assessment) Tool to help answer these questions for specific practices.
The SRA Tool is intended to help small and medium-sized healthcare providers and their partners, including those involved in vendor risk management, generate risk assessments as required by the HIPAA Security Rule. It enables organizations to perform a quick, internal HIPAA risk assessment by walking users through a series of prompts and questions.
The new SRA Tool version 3.3 has just been released with a version for Windows and a version in the form of an Excel workbook. The update incorporates Health Industry Cybersecurity Practices (HICP) references, bug fixes, and file association in Windows.
In this blog post, we’ll provide background on HIPAA and dive deeper into the version 3.3 SRA Tool and how it can benefit your organization.
What is HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) protects sensitive patient information. It outlines strict protocols that companies handling or encountering Protected Health Information (PHI) must adhere to.
What is the HIPAA Security Rule?
The HIPAA Security Rule defines requirements for protecting electronic PHI (ePHI) such as electronic medical records to ensure you are storing, using, and sharing sensitive electronic patient data securely and legally.
The requirement for Covered Entities and Business Associates to conduct a HIPAA risk assessment is included in the HIPAA Security Rule, and was first introduced in 2003.
Covered Entities are defined as (1) health plans, (2) health care clearinghouses, and (3) health care providers who electronically transmit any health information in connection with transactions for which HHS has adopted standards.
Business Associates are defined as a person or entity, other than a member of the workforce of a Covered Entity, who performs functions or activities on behalf of, or provides certain services to, a Covered Entity that involve access by the Business Associate to PHI. A subcontractor that creates, receives, maintains, or transmits PHI on behalf of another Business Associate is also considered a Business Associate.
How Does the SRA Tool Work?
The SRA Tool provides a great way to do a quick, internal risk assessment that helps you understand risks to the confidentiality, integrity, and availability of PHI. It can be downloaded here at no cost.
SRA version 3.3 for Windows is divided into three steps:
- Entering practice information
- Answering assessment questions
- Reviewing the risk report
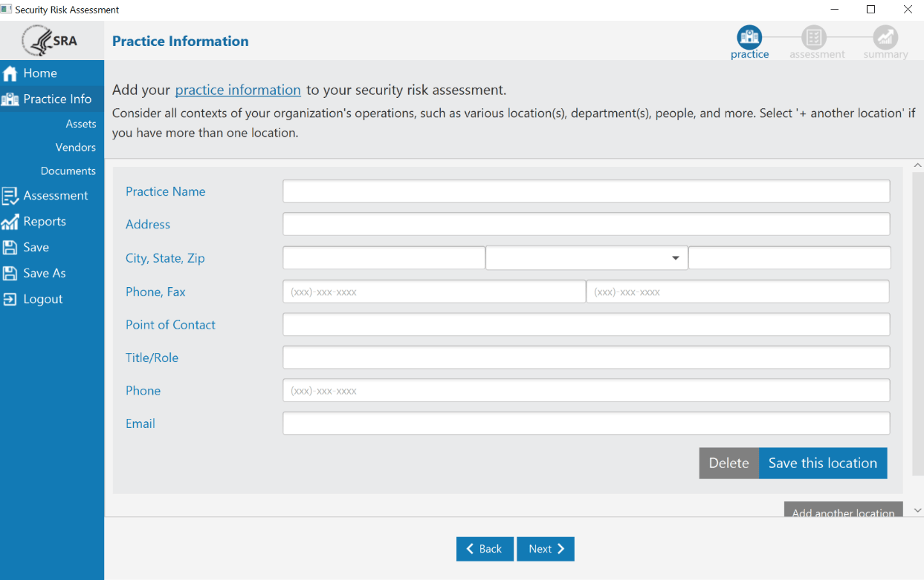
Practice Information
For the Practice Information section, you enter the asset inventory for your practice, vendors involved, and documents for upload.
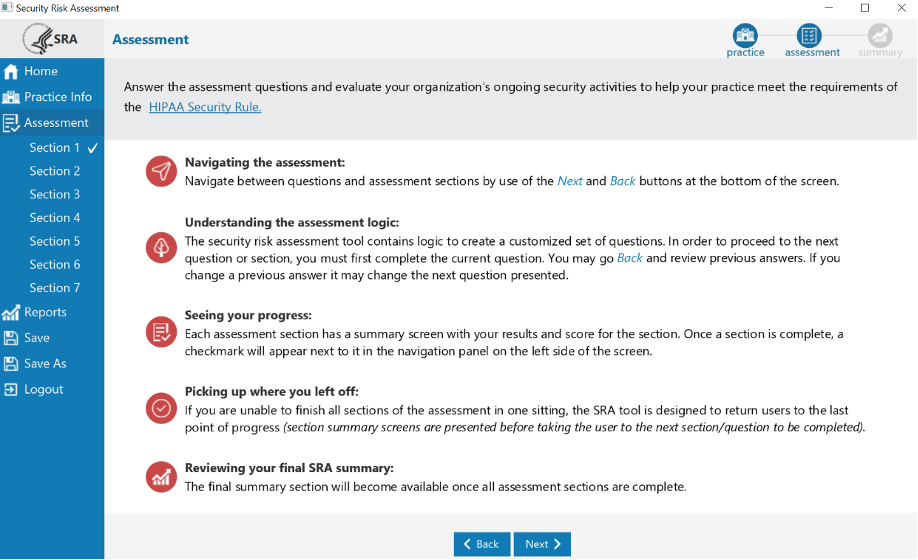
Assessment Questions
The questions in the Assessment section are divided into seven sections.
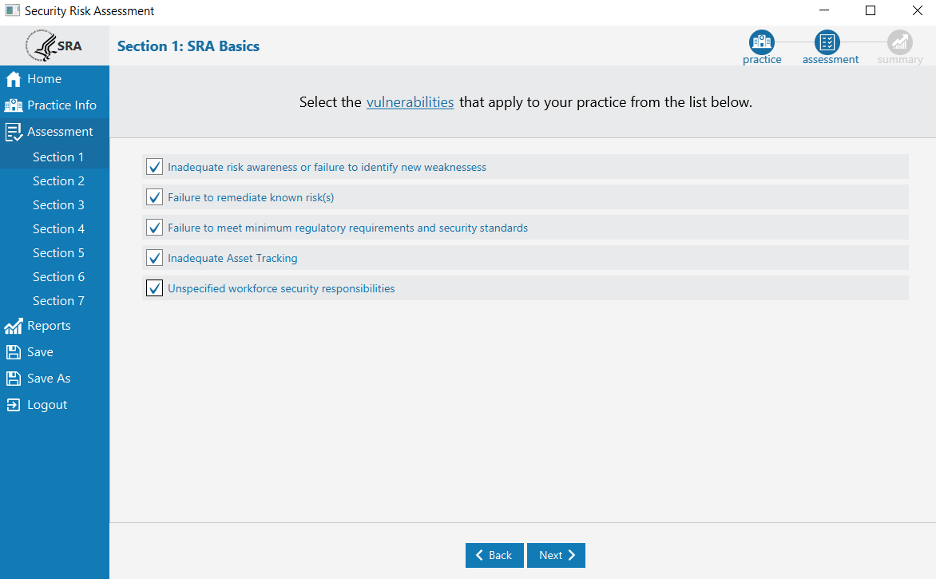
Each section has a list of questions. After answering those questions, you will select vulnerabilities that apply to your practice.
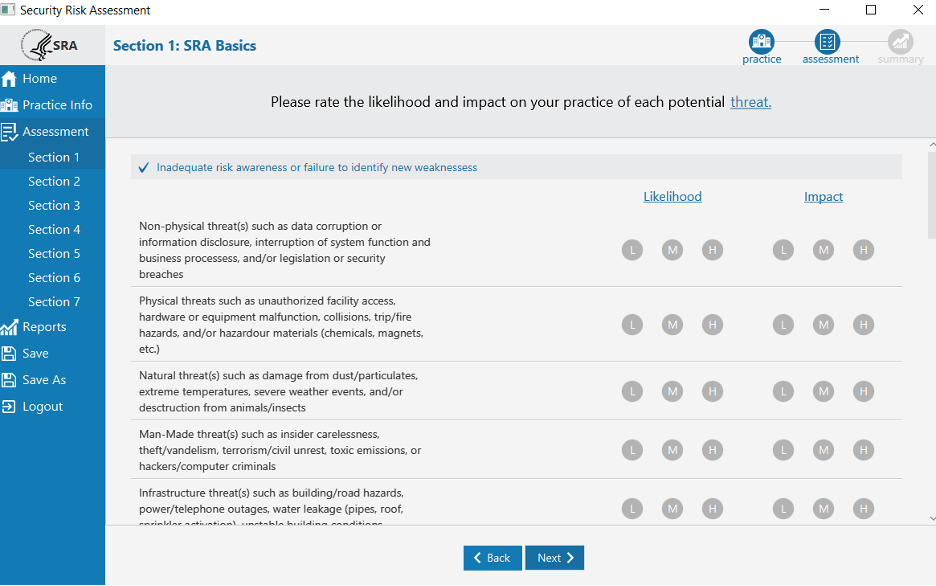
Based on the vulnerabilities selected, a list of threats will appear. Your job is to fill out the likelihood and impact for each threat (this is dependent on the practice since every organization has different structures, geographic locations, systems, etc.).
After filling this out, you will be taken to a page with two columns categorized by Areas of Success and Areas for Review. The Areas for Review column indicate what issues need to be addressed.
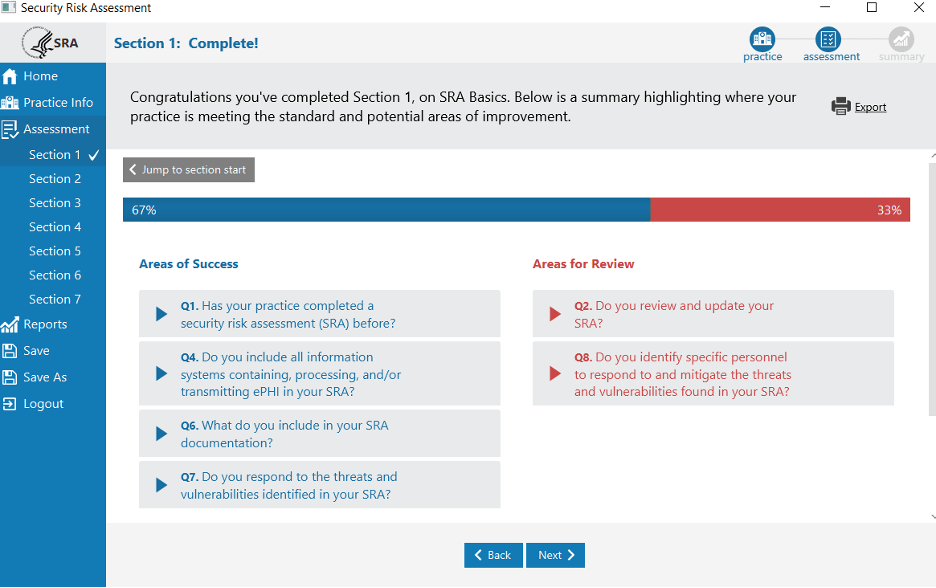
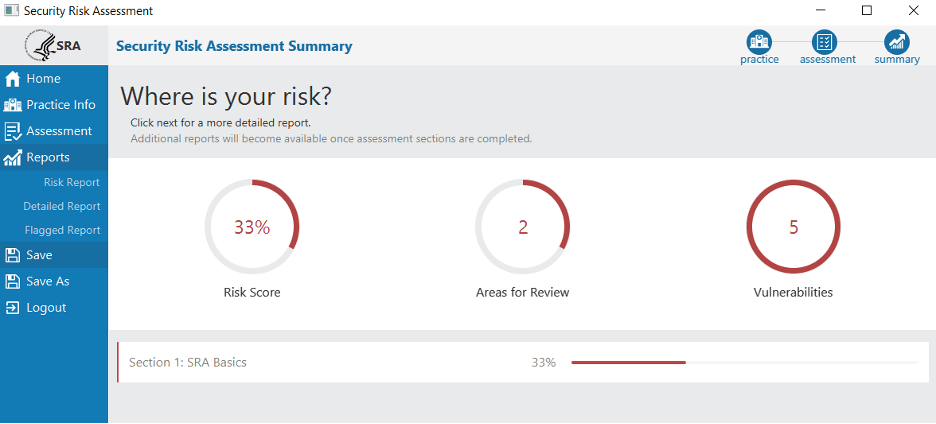
Risk Report
When you are finished, you’ll be presented with the Risk Report, which includes the Risk Score, Areas for Review, and Vulnerabilities.
Excel Worksheet Version
The Excel worksheet version of the SRA Tool is similar to the Windows version, only in worksheet format. There are multiple Excel sheets (1 for each section) with the threats and vulnerabilities given at the bottom of each section. The only difference is that the Excel worksheet does not have the asset inventory, vendor, or document upload.
We Can Help
While the SRA Tool is an excellent resource for helping small and medium-sized Covered Entities and Business Associates perform a quick internal risk assessment, it is not meant for all healthcare providers. And it is not guaranteed to satisfy the risk assessment requirement in the HIPAA Security Rule. We can work with you to review your SRA Tool results to determine whether you meet the Security Rule requirement. If not, we recommend that you have Tevora conduct an in-depth external risk assessment. When conducting risk assessments, our team incorporates our own HydraRisk Model which tailors the risk assessment specifically to your environment. Our HydraRisk model incorporates the best of widely accepted risk assessment models including Factor Analysis of Information Risk (FAIR), Operationally Critical Threat, Asset, and Vulnerability Education (OCTAVE), and National Institute of Standards and Technology (NIST) 800-30. For more information on the HydraRisk model, refer to HydraRisk.
Tevora’s security experts have an in-depth understanding of HIPAA, the SRA Tool, and the latest updates from HHS, and we would be happy to help you perform a full risk assessment. And even if your risk assessment meets the Security Rule requirement, our team can provide other services to help you achieve and maintain HIPAA compliance, including:
- Full HIPAA Gap Assessment
- Conduct interviews and review processes, systems, controls, and documentation related to handling of ePHI data.
- Identify areas that fall short of requirements defined in the HIPAA Security Rule.
- Prepare HIPAA Gap Analysis Report documenting gaps and recommending remediation steps.
- Remediation
- Remediate gaps identified in Gap Assessment.
- Tevora partners with you to perform this work, which may range from writing security policies to implementing security controls.
- HIPAA Attestation
- When remediation work is complete, conduct review of environment to assess compliance with HIPAA requirements.
- Prepare HIPAA Security Rule Attestation Letter confirming your compliance with HIPAA security requirements.
Additional Resources
Below are additional resources that provide a deeper dive into the topics covered in this blog post:
- SRA Tool Update
- SRA Tool Version 3.3 Download and Information
- Tevora Webinar: How to Become HIPAA Compliant: An Introduction to the HIPAA Security Rule
- Blog Post: 4 Tips for a Successful HIPAA Risk Assessment
- Blog Post: 5 Steps to Successful HIPAA Compliance for Self-Insured Group Health Plans
Contact Us
If you have questions about the SRA Tool or HIPAA requirements, or would like help bringing your organization into compliance with this important security standard, just give us a call at (833) 292-1609 or email us at sales@tevora.com.




