Navigating NIST–Which Standards Apply to You?
By Andrew Katz
The National Institute of Standards and Technology (NIST) develops cybersecurity standards, guidelines, best practices, and other resources to meet the needs of U.S. industry, federal agencies, and the broader public.
NIST standards apply to many industries and types of organizations, with some of the most widely-adopted standards being NIST CSF, NIST 500-53, and NIST 800-171. In this blog post, we’ll provide an overview of each of these standards and help you decide which standard(s) apply to your organization.
NIST Cybersecurity Framework (CSF)
NIST CSF is a voluntary framework consisting of standards, guidelines, and best practices that help organizations manage cybersecurity risks.
NIST developed CSF to aid organizations in designing and strengthening their security programs, which helps protect U.S. critical infrastructure. The framework is divided into five separate functions. Each function has 23 categories, which are further divided into 108 controls or “outcomes”.
What Organizations Does NIST CSF Apply To?
This standard is relatively straightforward and ideal for organizations whose goal is to implement the foundations of a security program or to strengthen an existing program.
What Types of Information Systems Are Covered?
NIST CSF covers commercial and non-federal government systems across all service and deployment models, including physical IT environments, virtualized networks, and cloud systems/software.
What Are the NIST CSF Functions?
The five NIST CSF functions are summarized below:
NIST CSF Functions
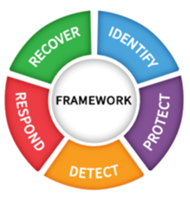
- Identify—Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
- Protect—Develop and implement the appropriate safeguards to ensure delivery of critical infrastructure services.
- Detect—Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
- Respond—Develop and implement the appropriate activities to take action regarding a detected cybersecurity incident.
- Recover—Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
NIST 800-53
NIST 800-53 provides a list of security and privacy controls for United States federal information systems except those related to national security. According to the Federal Information Security Management Act (FISMA), federal agencies must develop, document, and implement an information security and protection program using NIST 800-53 controls with Federal Information Processing Standards (FIPS) 199 and FIPS 200 as guidance.
FIPS Publication 199 requires agencies to categorize their information systems as low-impact, moderate-impact, or high-impact for the security objectives of confidentiality, integrity, and availability (CIA). The overall impact level must be the highest value of any of the three CIA categories. The specific set of NIST 800-53 controls for any particular system will vary depending on chosen security baseline.
What Organizations Does 800-53 Apply To?
NIST 800-53 is applicable for organizations that must comply with FISMA, FedRAMP, IRS 1075, StateRAMP, and other federal or state government laws and programs.
What Types of Information Systems Are Covered?
NIST 800-53 covers Commercial, Government, and Federal systems across all service and deployment models, including physical IT environments, virtualized networks, and cloud systems/software.
For more information on the new changes within NIST 800-53 Revision 5, see our recent blog post: Six Steps to NIST SP 800-53 Revision 5 Compliance
What Are the NIST 800-53 Control Families?
NIST 800-53 covers the following control families:
- AC – Access Control
- AT – Awareness and Training
- AU – Audit and Accountability
- CA – Assessment, Authorization, and Monitoring
- CM – Configuration Management
- CP Contingency Planning
- IA – Identification and Authentication
- IR – Incident Response
- MA – Maintenance
- MP – Media Protection
- PE – Physical and Environmental Protection
- PL – Planning
- PM – Program Management
- PS – Personnel Security
- PT – Personally Identifiable Information Processing and Transparency
- RA – Risk Assessment
- SA – System and Services Acquisition
- SC – System and Communications Protection
- SI – System and Information Integrity
- SR – Supply Chain Risk Management
NIST 800-171
NIST 800-171 provides recommended security requirements for the protection of Controlled Unclassified Information (CUI) resident in nonfederal systems and organizations. According to the Defense Counterintelligence and Security Agency, CUI is government-created or owned information that requires safeguarding or dissemination controls consistent with applicable laws, regulations, and government-wide policies. Personally Identifiable Information (PII) is one example of CUI.
Cybersecurity Maturity Model Certification (CMMC)is a training, certification, and third-party assessment program that the federal government has implemented to ensure that its contractors are adequately protecting CUI. CMMC is not entirely synonymous with NIST 800-171, although contractor organizations may be required to implement NIST 800-171 controls based on the CMMC “level” they must adhere to. For more information on CMMC 2.0 and how its upcoming changes may affect you, see our recent blog post: CMMC 2.0 Eases Compliance Burden for DoD Contractors and Subcontractors.
What Organizations Does NIST 800-171 Apply To?
NIST 800-171 applies to federal government contractors and sub-contractors.
Department of Defense (DoD)contractors should implement the controls in NIST 800-171 to protect CUI included in their defense contracts, as required by Defense Federal Acquisition Regulation Supplement (DFARS) clause 252.204-7012. Additionally, this requirement must flow down to any subcontractors within the contractor’s supply chain.
What Are the NIST 800-171 Control Families?
NIST 800-171 covers the following control families:
- Access Control
- Awareness and Training
- Audit and Accountability
- Configuration Management
- Identification and Authentication
- Incident Response
- Maintenance
- Media Protection
- Physical Protection
- Personnel Security
- Risk Assessment
- Security Assessment
- System and Communications Protection
- System and Information Integrity
Tevora Can Help
Our experienced security experts can partner with you to bring your organization into compliance with NIST CSF, NIST 800-53, or NIST 800-171, ensuring readiness for any ISO audit or compliance assessment, depending on your specific needs and the laws and regulations that apply to your business.
Tevora is an accredited ISO 17020 inspection body[1] and is fully qualified to assess your compliance with all of these standards.
If you have questions about any of the NIST standards described in this blog post or would like help bringing your organization into compliance, just give us a call at (833) 292-1609 or email us at sales@tevora.com.
[1] As accredited by A2LA R335 Specific Requirements – Cybersecurity Inspection Body Program




