June 12, 2024
Exploring New Dimensions of Supply Chain Security in NIST CSF 2.0
2023 Saw a Surge of Software Supply Chain Attacks
In 2023, the cybersecurity landscape witnessed a dramatic surge in software supply chain attacks, surpassing the combined numbers of the previous three years. With businesses grappling with a staggering $46 billion in costs to address 245,000 supply chain incidents, the severity of the threat became undeniable. The State of Application Security Posture Management (ASPM) 2024 report revealed that 77% of US-based CISOs identify software supply chain security as a glaring blind spot within their application security strategies. The crux of the problem is AppSec’s narrow focus on vulnerabilities when the real threat lies in the spread of malware. Although vulnerabilities grew in 2023, they were eclipsed by the exponential increase in supply chain attacks, predominantly stemming from malware. This paradigm shift calls for a comprehensive reevaluation of cybersecurity strategies, emphasizing the imperative of addressing the broader spectrum of threats from the software supply chain.
Notable Supply Chain Vulnerabilities
Hackers continue to capitalize on vulnerabilities within the software supply chain, orchestrating numerous widespread attacks. Amidst the focus on patching zero-day vulnerabilities favored by ransomware groups, the critical risks associated with the software supply chain have been neglected.
Some of the most noteworthy recent attacks are:
XZ Utils – XZ Utils is a widely used tool for lossless data compression on Unix-like systems. Andres Freund, a developer working on Microsoft’s PostgreSQL, identified performance issues in a Debian system’s SSH caused by these updates, ultimately leading to the revelation of the backdoor on the Open Source Security List.
JetBrains – Groups from North Korea and Russia exploited a critical vulnerability (CVE-2023–42793) in JetBrains TeamCity, a widely used CI/CD tool. The attack targeted high-value links in software supply chains, affecting organizations globally across various sectors.
MOVEit – MOVEit, a managed file transfer (MFT) software, was subject to multiple vulnerabilities (CVE-2023-34362, CVE-2023-35036, CVE-2023-35708), including SQL injections. This attack posed significant supply chain risks and allowed threat actors to extract, manipulate, or delete data from the victim’s database.
Although the list of cyberattacks and data breaches above has been greatly abbreviated, none of them seem to be slowing down in 2024.
In light of this growing trend, NIST has released an updated Cybersecurity Framework, NIST CSF 2.0, with a stronger focus on enhancing supply chain risk management. This version provides additional guidance to help organizations tackle the rising threat of supply chain attacks amidst growing global interconnectivity.
New Additions to Cybersecurity Supply Chain Risk Management
The CSF 2.0 comes updated with six core functions from the previous five: Govern, Identify, Protect, Detect, Respond, and Recover. The most significant addition to NIST CSF 2.0 being the GOVERN function, which focuses on developing, communicating, and monitoring the organization’s cybersecurity risk management strategy, expectations, and policies. The GOVERN function is vital in determining what an organization should prioritize and execute to achieve the outcomes of the other five tasks in the framework. The GOVERN function expands upon CSF 1.1 by understanding organizational context, defining cybersecurity strategies, developing policies, implementing cybersecurity strategy, and managing cybersecurity supply chain risk management (C-SCRM).
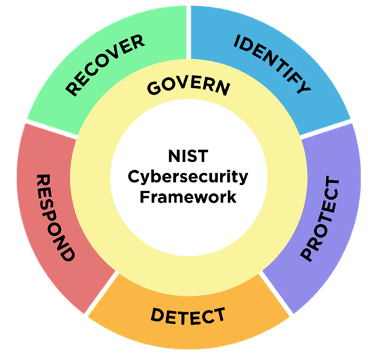
Figure 1 – NIST CSF 2.0 Functions Source: NIST
NIST CSF’s GV.SC Category
The GV.SC (Cybersecurity Supply Chain Risk Management) category offers a structured way of managing supply chain risks.
“The primary objective of C-SCRM is to extend appropriate first-party cybersecurity risk management considerations to third parties, supply chains, and products and services an organization acquires, based on supplier criticality and risk assessment.”
– NIST CSF 2.0
Below are the 10 sub-categories within C-SCRM:
GOVERN (GV): The organization’s cybersecurity risk management strategy, expectations, and policy are established, communicated, and monitored.
Cybersecurity Supply Chain Risk Management (GV.SC): Cyber supply chain risk management processes are identified, established, managed, monitored, and improved by organizational stakeholders.
GV.SC-01: A cybersecurity supply chain risk management program, strategy, objectives, policies, and processes are established and agreed to by organizational stakeholders.
GV.SC-02: Cybersecurity roles and responsibilities for suppliers, customers, and partners are established, communicated, and coordinated internally and externally.
GV.SC-03: Cybersecurity supply chain risk management is integrated into cybersecurity and enterprise risk management, risk assessment, and improvement processes.
GV.SC-04: Suppliers are known and prioritized by criticality.
GV.SC-05: Requirements to address cybersecurity risks in supply chains are established, prioritized, and integrated into contracts and other types of agreements with suppliers and other relevant third parties.
GV.SC-06: Planning and due diligence are performed to reduce risks before entering into formal supplier or other third-party relationships.
GV.SC-07: The risks posed by a supplier, their products and services, and other third parties are understood, recorded, prioritized, assessed, responded to, and monitored over the course of the relationship.
GV.SC-08: Relevant suppliers and other third parties are included in incident planning, response, and recovery activities.
GV.SC-09: Supply chain security practices are integrated into cybersecurity and enterprise risk management programs, and their performance is monitored throughout the technology product and service life cycle.
GV.SC-10: Cybersecurity supply chain risk management plans include provisions for activities that occur after the conclusion of a partnership or service agreement.
CSF 2.0 Tools that Help Organizations Address Supply Chain Risk
CSF 2.0 also brings significant updates in the guidance and resources offered, providing a suite of customizable tools for organizations to adapt as their needs and capabilities change over time. This flexibility enables organizations to modify their use of the CSF according to evolving circumstances without being restricted to a single approach.
CSF 2.0 Profiles
Previously, profiles primarily served the purpose of aiding organizations in sharing security goals and outcomes, fostering collaboration to enhance risk management processes within defined parameters. CSF 2.0 further improved profiles with the addition of organizational and community profiles. Community Profiles harness the collective expertise of diverse organizations to create shared cybersecurity risk management blueprints. Implementing Community Profile Lifecycles signals a dynamic evolution in profile management, encompassing planning, development, utilization, and maintenance phases. By participating in Communities of Interest, smaller businesses can now leverage collective insights and perspectives tailored to their specific use cases or industries, enriching their understanding of cybersecurity challenges and solutions.
These profiles, created in partnership with various industries such as financial institutions, healthcare entities, and educational institutions, use the CSF’s everyday language and are based on real-world applications and shared challenges in these communities. The NIST National Cybersecurity Center of Excellence (NCCoE) facilitates the creation of these profiles, which are subsequently housed in the NCCoE’s Framework Profile Resource Center, where companies can gain valuable insights and recommendations to improve their cybersecurity posture. NIST offers these templates to assist organizations in building their profile.
CSF 2.0 Community and Organizational Quick Start Guides
The Guide to Creating Community Profiles offers insights and considerations for creating and utilizing Community Profiles to implement CSF
2.0 effectively. The guide covers the Community Profile Lifecycle (Plan, Develop, Use, Maintain), which provides a process for creating a community profile. It begins with a thorough planning phase, where the community’s needs are understood, and the scope of the Profile is defined. This thoughtful planning informs the development process, resulting in the creation of the Community Profile. Once developed, the Profile is made available for use by organizations within the community. Periodic reviews and updates ensure that the Profile remains relevant and effective over time, with communication playing a crucial role in coordinating and collaborating among organizations throughout its lifecycle.
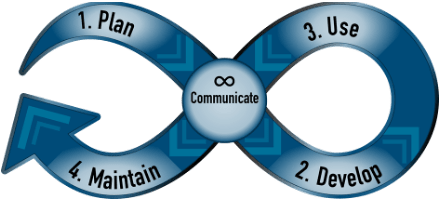
Figure 3 – Community Profile Lifecycle Source: NIST
Additionally, NIST offers a Quick-Start Guide for Creating and Using Organizational Profiles. These profiles are used to design, assess, and prioritize cybersecurity outcomes according to an organization’s mission objectives, stakeholder expectations, and threat landscape. The guide covers how organizations can manage cybersecurity risks strategically and analyze progress over time by comparing existing and target profiles, conducting gap analysis, and defining action plans. The guide also outlines a five-step process for creating and using Organizational Profiles, emphasizing the importance of ongoing monitoring, feedback loops, and communication.
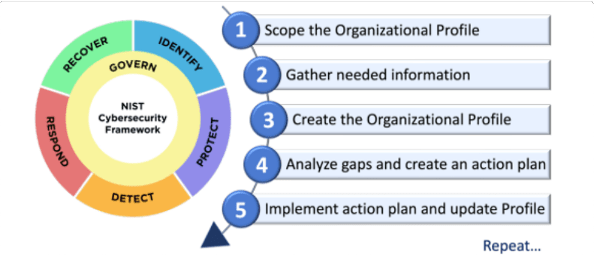
Figure 4 – Steps for Creating and Using Organizational Profiles Source: NIST
CSF 2.0 C-SCRM Quick Start Guide
The NIST CSF 2.0 Cybersecurity Supply Chain Risk Management (C-SCRM) Quick Start Guide defines a systematic approach to managing cybersecurity risk across supply chains, including strategies, processes, and procedures. This guide applies to organizations of all sizes, particularly those that rely on information and communications technology (ICT) products and services. Organizations can address issues such as malicious functionality, counterfeit devices, and vulnerabilities stemming from poor manufacturing practices within the supply chain by identifying, assessing, and mitigating risks.
Figure 4 – NIST CSF 2.0 Quick Start Guidance Document for C-SCRM Source: NIST
The C-SCRM capability outlined in CSF 2.0 requires collaboration and communication among stakeholders across the enterprise to secure favorable outcomes. Specifically, the guide offers actionable checklists for activities such as creating a C-SCRM strategy, identifying technology suppliers, and establishing organizational roles and requirements. The guide further emphasizes the importance of establishing security requirements for suppliers, integrating cybersecurity responsibilities into organizational policies and agreements, and implementing monitoring mechanisms throughout the supplier relationship lifecycle.
Implementing the practices outlined in the guide will significantly benefit organizations and enhance their resilience against cybersecurity threats within the supply chain ecosystem. Furthermore, the guide facilitates alignment between functions contributing to C- SCRM management, promotes transparency in supplier relationships, and empowers organizations to tailor their cybersecurity requirements based on supplier criticality levels. The guide is a valuable resource for organizations seeking to strengthen their cybersecurity posture and mitigate risks associated with the increasingly complex and interconnected supply chain landscape.
Tevora Can Help
Tevora can help organizations develop and implement effective supply chain risk management strategies that are consistent with the principles laid out in CSF 2.0. Our experts are skilled in conducting detailed assessments to identify potential supply chain vulnerabilities, designing specific risk mitigation plans, and aiding with implementing controls and processes that improve supply chain resilience. Tevora can also advise on incorporating supply chain risk management strategies into current cybersecurity frameworks, guaranteeing comprehensive coverage and compliance with industry standards. This process can start with an evaluation of the organization’s existing supply chain risk management process, highlighting program-level gaps and ensuring that best practices are followed.
If you have questions on managing or assessing supply chain risk in your organization, our experienced experts at Tevora can help. Just give us a call at (833) 292-1609 or email us at sales@tevora.com.